WYSK: 11/19/21
This week: 1. Peng Shuai; 2. ASAT Test; 3. Ring Monitoring; 4. Hack Back

What you should know from the week of 11/19/21:
- Peng Shuai: Chinese tennis star 'disappeared' after accusing high-ranking Chinese politician of sexual assault;
- ASAT Test: Russia conducts an anti-satellite test, creating new space debris;
- Ring Monitoring: LAPD requests for Ring footage harms norms of freedom of expression in the US;
- Hack Back: Hack Back may be appealing, but the harms exceed the benefits.
Peng Shuai:

Peng Shuai, a Chinese tennis star, publicly accused a Chinese government official—former Vice Premier Zhang Gaoli—on the social media site Weibo of sexual assault. She has not been heard from since.
The tennis star has not been heard from since she made sexual assault allegations against a top Chinese government official two weeks ago.
Her post on Weibo was removed minutes after it was posted, and Weibo users can no longer comment on her posts.
Chinese State Media CGTN (China Global Television Network) released a screenshot of an email purportedly from Peng denying the accusations. The release appears obviously unconvincing, and is deeply concerning in context of Peng's accusations and her censorship online.
The Women's Tennis Association (WTA) Chairman and CEO noted that the CGTN release only increases his concern, and the WTA has expressed willingness to pull out of China. WTA has taken the strongest stance against this, and has called for a full investigation. The International Olympic Committee has failed to take action, instead supporting "quiet diplomacy" and refusing to comment further.
The Chinese government has responded to questions about Peng's whereabouts and wellbeing through a Foreign Ministry spokesperson saying that such a question is “not a diplomatic question and I’m not aware of the situation.”
China's human rights abuses continue to grow in scale and visibility. The international community needs to support Chinese individuals who speak out against government abuses.
ASAT Test:

Russia tested an anti-satellite (ASAT) weapon that destroyed a Russian satellite, blowing it up and creating a large debris field:
Russia tested a direct-ascent anti-satellite (DA-ASAT) missile on Nov. 15, 2021, Moscow Standard Time, that struck a Russian satellite [COSMOS 1408] and created a debris field in low-Earth orbit. The test so far has generated more than 1,500 pieces of trackable orbital debris and will likely generate hundreds of thousands of pieces of smaller orbital debris.
That distinction between trackable and untrackable debris is critical . As NASA notes, not all debris is trackable:
More than 27,000 pieces of orbital debris, or “space junk,” are tracked by the Department of Defense’s global Space Surveillance Network (SSN) sensors. Much more debris -- too small to be tracked, but large enough to threaten human spaceflight and robotic missions -- exists in the near-Earth space environment. Since both the debris and spacecraft are traveling at extremely high speeds (approximately 15,700 mph in low Earth orbit), an impact of even a tiny piece of orbital debris with a spacecraft could create big problems.
NASA goes on to note that even paint flecks can cause significant damage to spacecraft and that:
In fact, millimeter-sized orbital debris represents the highest mission-ending risk to most robotic spacecraft operating in low Earth orbit.
An added 1,500 trackable pieces of debris is an increase of about 5.5% of all trackable space debris: a huge increase from one nation's intentional actions.
Space debris remains for years or decades, and each item of debris increases the likelihood of producing more debris in a runaway chain reaction called Kessler Syndrome, ultimately threatening humanity's ability to operate in space.
Ring Monitoring:

From the Electronic Frontier Foundation this week, Matthew Guariglia and Dave Maass report on LAPD requests for Ring camera footage:
According to emails obtained by EFF, the LAPD sent requests to Amazon Ring users specifically targeting footage of Black-led protests against police violence that occurred in cities across the country last summer.
By forming partnerships with Ring users, police departments can conduct intrusive surveillance while sidestepping normal warrant or subpoena legal checks. As I wrote in October: "While Ring is allegedly a home protection tool, its massive scale, features, and marketing endow it with additional capabilities that make it something more than a mere tool for home protection."
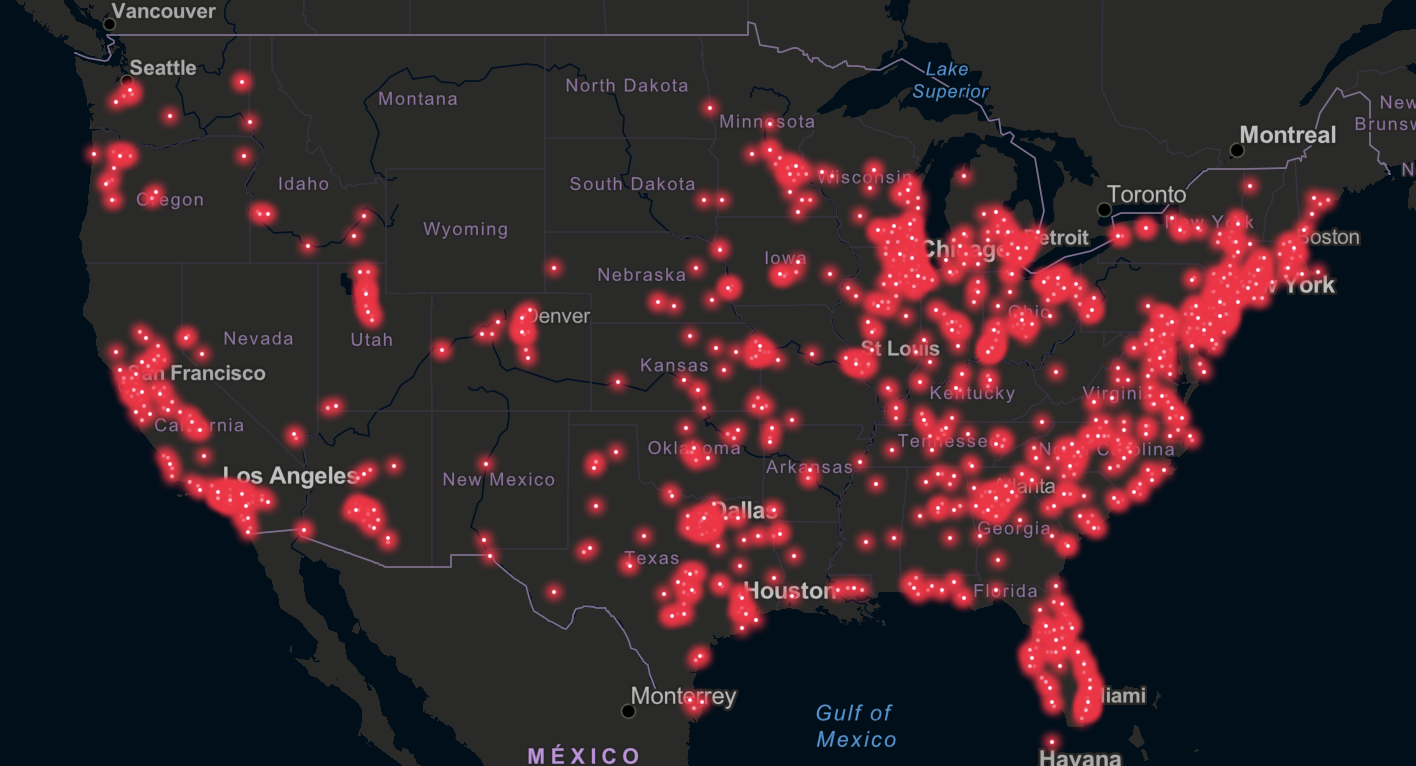
The LAPD made requests for all footage captured by Ring doorbells during an undisclosed time period. As EFF notes:
This practice is concerning, because if police request hours of footage on either side of a specific incident, they may receive hours of people engaging in First Amendment protected activities with a vague hope that a camera may have captured illegal activity at some point.
Ring cameras are so common in the US that it Ring presents specific challenges to free expression:
[Ring's ubiquity] poses an incredible risk to First Amendment rights. People are less likely to exercise their right to political speech, protest, and assembly if they know that police can acquire and retain footage of them.
Hack Back:

This week, MalwareTech (Marcus Hutchins) wrote an article about hack back:
"an umbrella term for various proposed [legal] exceptions to...allow security experts to engage in retaliatory hacking against criminal actors, for purposes such as attribution or disruption."
Hutchins is famous for his critical work disarming the WannaCry attack, as well as his arrest by the FBI for writing malware and supporting cybercrime in his youth Andy Greenberg has written an exhaustive article on Hutchins. The TL;DR on Hutchins is that he did engage in cybercrime as a youth, but moved away from that activity and is an 'upstanding citizen' today.
In his analysis Hutchins notes:
At the core of all these beliefs is that by leveling the playing field, defenders could better respond to intrusions and deter attacks.
But that proposals to allow hack back have critical flaws related to:
- Prosection: laws allowing hack back create new legal challenges. What happens if a someone, while hacking back, causes additional damage to another victim?
- Conflicts of Interest: Uncoordinated active defense can work against long-term law enforcement goals.
- Perverse Incentives: Security companies and criminals might start a de-facto war, increasing the harms experienced by businesses and individuals.
- Existing capabilities: The government already can and does authorize private companies to engage in botnet takedowns today.
Finally, Hutchins makes his best point:
Currently there exists a major blind spot in the government’s ability to respond to cyberattacks...[This] immunity window exists when a threat actor is shielded from law enforcement by their home nation; however, they do not meet the threshold for classification as either a state actor or a national security threat. This is the sweet spot in which many ransomware actors operate.
The US government is failing to effectively respond to actors in this 'immunity window.' Authorizing hack back would not address the root issues (the US government needs to take action against malign actors) but would introduce new harms and complications.
Interest piqued? Disagree? Reach out to me at TwelveTablesBlog [at] protonmail.com with your thoughts.
Photo by Tamara Gak on Unsplash
